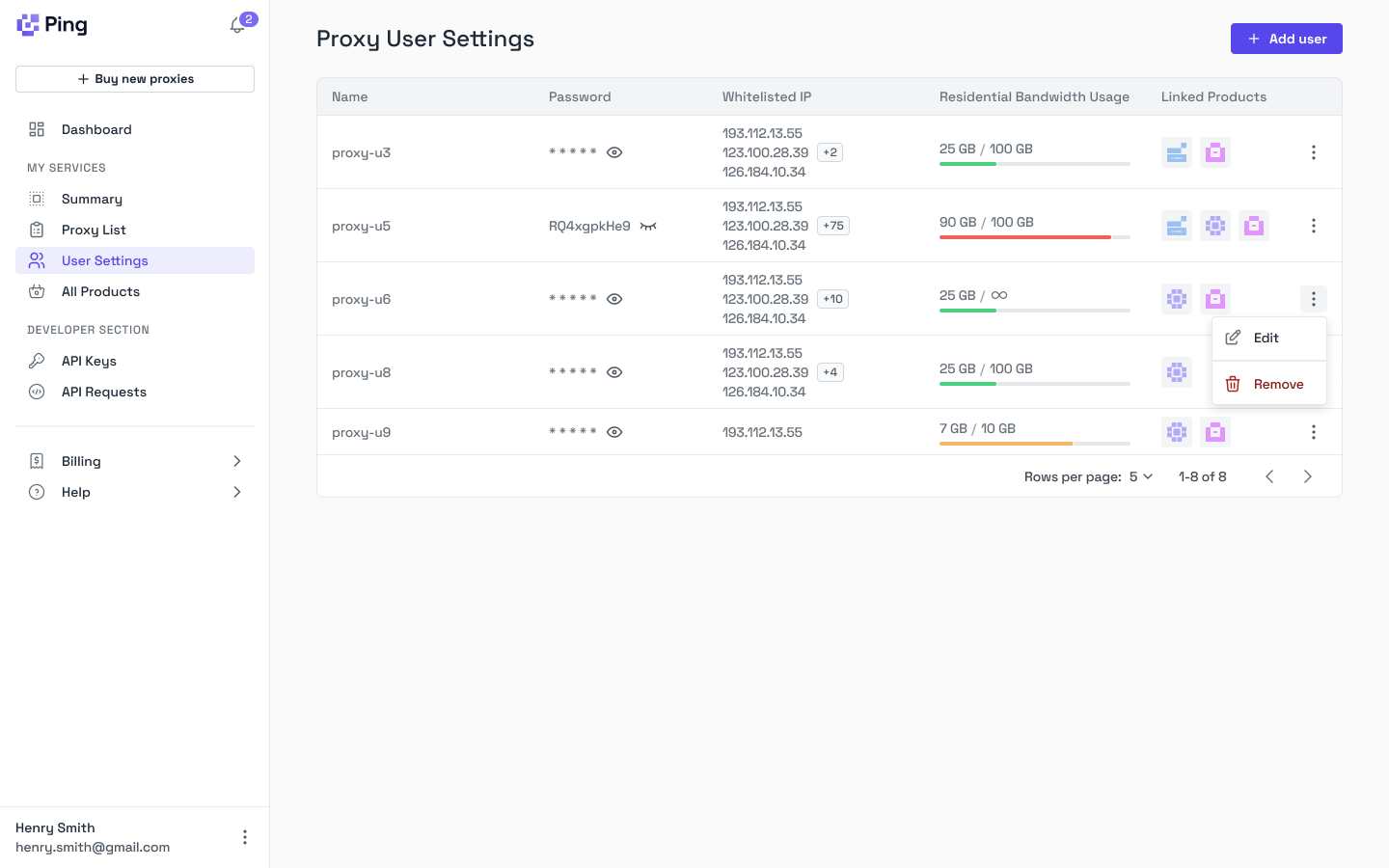
 Ping Proxies supports multiple authentication methods to provide flexible, secure access to your proxies. Our innovative Proxy User and IAM system lets you create and manage proxy users, track their usage, limit residential bandwidth, and link their access to specific proxies and services—all from our dashboard.
Ping Proxies supports multiple authentication methods to provide flexible, secure access to your proxies. Our innovative Proxy User and IAM system lets you create and manage proxy users, track their usage, limit residential bandwidth, and link their access to specific proxies and services—all from our dashboard.
Authentication Methods
Proxy User Authentication
This authentication type allows you to create a Proxy User and access all available proxies using their username and password credentials.
- Benefits: Use consistent credentials across all your proxies
- Recommended for: Resellers who want to assign each customer a dedicated proxy user with access to specific services
IP Authentication
With IP authentication, you can access your static proxies without entering username and password credentials. This method works by:
- Creating a proxy user
- Attaching a whitelisted IP address to that user for authentication
Important: Each whitelisted IP address must be unique and cannot be assigned to multiple proxy users.
IP Authentication is not available on our rotating residential bandwidth network since the username parameters are used to inter targeting and geolocation settings.

